Archived research projects in CRoCS laboratory
Below, you can find older projects, which are not currently actively pursued further, but may be activated again later (as happened for multiple projects already).
Disk encryption
 The first goal is research, and implementation of new algorithms (key derivation, authenticated encryption or integrity protection mechanism) into existing open-source LUKS/cryptsetup disk encryption project.
The first goal is research, and implementation of new algorithms (key derivation, authenticated encryption or integrity protection mechanism) into existing open-source LUKS/cryptsetup disk encryption project.
The second goal is to make LUKS/libcryptsetup (and supported FDE formats) truly multiplatform tool (Windows/Linux) with focus to independent and extensible open-source software based FDE (Full Disk Encryption) solution.
Contact: Milan Brož xbroz@fi.muni.cz
- Research project internal wiki pages
- Upstream (Linux) project homepage, GitHub mirror
Join us! The possible areas for cooperation:
- Developing HMI (Human-machine interface) for storage encryption - ease of use, test cases, simple GUI, HMI usability experiments.
- Disk (sector-level) storage encryption in Windows study, existing approaches and implementations (TrueCrypt, DiskCryptor, Bitlocker, FreeOTFE, …) with focus on free and open-source solutions. Windows driver architecture for implementing similar encryption capabilities as provided in Linux dm-crypt module.
- Windows boot process analysis and possibilities to use open-source boot loaders like GRUB2 to inject boot of core Windows system from (LUKS) encrypted device.
- Using open-source multiplatform encryption libraries (gcrypt, openssl, etc) for implementation of symmetric block cipher encryption wrappe in windows environment, both in userspace and driver.
- Current status quo in RNG available in Windows7 and later systems, implementation of wrapper (or usable alternative) to Linux /dev/[u]random device.
- Milan Brož 2014-now (Project lead and coordinator, Red Hat cooperation, grumbling)
- Ondrej Mosnáček 2015-now
- Agáta Dařbujanová 2014-2016 (Student, User interface for storage encryption application)
Selected publications:
- [2016] Harčár, M.: Generátory náhodných čísel v multiplatformním prostředí, FI bachelor thesis
- [2016] Dařbujanová, A.: Uživatelské rozhraní aplikace pro šifrování disku, FI bachelor thesis
- [2016] Brož M.,Kozina,O.: The Future of Disk Encryption with LUKS2, DevConf 2016
- [2015] Brož M.,Matyáš V.: Selecting a New Key Derivation Function for Disk Encryption, STM 2015
- [2015] Mosnáček, O.: Key derivation functions and their GPU implementations, FI bachelor thesis
- [2014] Brož M.,Matyáš V.: The TrueCrypt On-Disk Format—An Independent View, IEEE Security & Privacy, 2014, vol. 12, No 3, p. 74-77. ISSN 1540-7993
- [2011] Brož M.:Disk encryption (not only) in Linux, Europen.cz 2011, Red Hat DevConf 2012
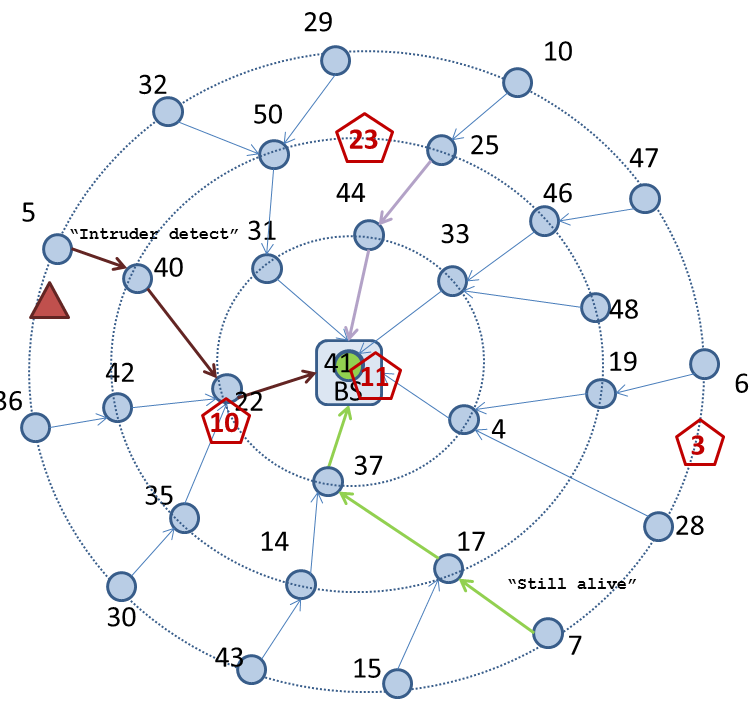
Wireless Sensor Networks
This project includes providing a secure platform that is transparent for applications in wireless sensor networks (WSN) - WSNProtectLayer. Our platform includes intrusion detection system (IDS) detecting active attacks. We consider privacy issues to prevent passive attacks on the WSN. We also propose secrecy amplification protocols and evaluate key management schemes. Current work includes parametrised attacker simulated on KMSforWSN framework.
Contact: Lukáš Němec lukas.nemec@mail.muni.cz
Additionally, we are developing an optimization framework for the IDS incorporating MiXiM simulator. Evolutionary algorithms are used to optimize the IDS's performance.
- Research project internal wiki pages
- WSNProtectLayer - security middleware for TinyOS
- virtual radio is simulated and automatic packet protection, IDS and key management is provided.
- WSNProtectLayer Github repository
- Take a look at video showing WSNProtectLayer middleware in action.
- Secrecy amplification protocols
- establishing secure links in partially compromised network
- SensorSim simulator download page - fast simulator optimized for simulation of secrecy amplification protocols and probabilistic key predistribution
- KMSforWSN framework based on OMNet++ simulator together with parametrised attacker specification
- Laboratory testbed
- Laboratory tesbed with 28 TelosB and 20 JeeNode nodes
- Lukáš Němec 2013-now (Crypto and Key management in TinyOS, Arduino testbed network, Edu-hoc)
- Radim Ošťádal 2013-now (Secrecy amplification protocols, parametrised attacker in)
- Petr Švenda 2004-now (Key management schemes, secrecy amplification protocols)
Former participants: Martin Stehlík 2010-2017 (IDS, simulators, optimization); Marek Sýs 2015 (secrecy amplification protocols); Filip Jurnečka 2010-2014 (Key management schemes), Marcel Gazdík 2012-2013 (ePIR&RFID hw readers), Dušan Klinec 2008-2014 (WSNProtectLayer core developer, a lot of network experiments), Jiří Kůr 2009-2014 (Privacy protection, key establishment), Tobiáš Smolka (testbed, omnetpp experiments, secrecy amplification), Andriy Stetsko (IDS in WSN)
Selected publications:
- [2019] Němec, L.; Matyáš, V;Ošťádal, R.; Švenda, P.; Palant P.-L.: Evaluating Dynamic Approaches to Key (Re-)Establishment in Wireless Sensor Networks, Sensors, 19-4, 2019
- [2018] Němec, L.; Ošťádal, R.; Švenda, P.; Matyáš, V.: Adaptive Secrecy Amplification with Radio Channel Key Extraction, 2018 14th International Conference on Distributed Computing in Sensor Systems (DCOSS), 2018.
- [2018] Němec, L.; Ošťádal, R.; Švenda, P.; Matyáš, V.: Entropy Crowdsourcing – Protocols for Link Key Updates in Wireless Sensor Networks, In 26th International Workshop on Security Protocols (SPW 2018). Lecture Notes of Computer Science. Springer.
- [2016] Ošťádal, R.; Švenda, P.; Matyáš, V.: Reconsidering Attacker Models in Ad-hoc Networks, In 24th International Workshop on Security Protocols (SPW 2016). Lecture Notes of Computer Science. Springer.
- [2015] Ošťádal, R.; Švenda, P.; Matyáš, V.: On Secrecy Amplification Protocols, In 9th WISTP International Conference on Information Security Theory and Practice, LNCS 9311, Springer, pp. 3-19, 2015.
- [2014] Ošťádal, R.; Švenda, P.; Matyáš, V.: A new approach to secrecy amplification in partially compromised networks, In 4th International Conference on Security, Privacy and Applied Cryptography Engineering, LNCS 8804, Springer, pp. 92–109, 2014.
Software Security and Secure Programming
This project focuses on usage, evaluation and extension of various tools related to secure programming, application vulnerabilities, security testing and code review. We are interested in static and dynamic analysis of applications with a special focus on security bugs, fuzzy testing, taint analysis and semi-automated review procedures and its incorporation into application development lifecycle. This project is coordinated with Y Soft Corporation, a.s., and for students participating in this project, there is a possibility to get a financial support from this company. More general information about Y Soft cooperation with students can be found here.
Contact: Andriy Stetsko xstetsko@fi.muni.cz or andriy.stetsko@ysoft.com
Financial support: Y Soft Corporation, a.s. will provide financial support (in a form of stipend at the faculty or a part-time job in the company) to students with promising results.
Possible topics for cooperation with bachelor students:
Possible topics for cooperation with master students:
- Andriy Stetsko 2012-now (Project coordinator, thesis supervisor, Y Soft Corporation, a.s.)
Previous research topics:
- 2013-2017: Tools for dynamic security analysis of web applications, financial support from Y Soft Corporation
- 2015-2016: Analysis and application of OWASP testing guide, financial support from Y Soft Corporation
- 2015-2016: Metasploit, financial support from Y Soft Corporation
- 2014-2016: Secure software development processes, financial support from Y Soft Corporation
- 2012-2016: Tools for static and dynamic code analysis, financial support from Y Soft Corporation
- 2014-2015: Security mechanisms of PDF files
- 2014-2015: Security aspects of Xamarin/Android Platform
- Cesta project - security-related transformations of JavaCard source code, financial support from Y Soft Corporation
Faster randomness testing
This project is focused on improving the implementation of standard empirical test of randomness since some complete tests (Linear Complexity, Spectral, Overlapping template matching) can take hours on standard computer for usual amount of data. Tests are usually grouped into test batteries (NIST STS, Diehard,TestU01) to provide more complex randomness analysis. Currently we are focusing on optimization of NIST STS battery. Visit our online testing service.
Last update: 27.09.2016
Application Project Github repository
- Zdenek Říha 2013-now (Performance testing) zriha@fi.muni.cz;
- Marek Sýs 2013-now (Algorithm analysis) syso@mail.muni.cz
Publications
- [2015] Sýs, M.; Z. Říha, V. Matyáš, K.Márton, A. Suciu: On the Interpretation of Results from the NIST Statistical Test Suite, ROMJIST Journal, 2015.
- [2014] Sýs, M.; Z. Říha: Faster randomness testing with NIST STS,SPACE 2014, Fourth International Conference on Security, Privacy, and Applied Cryptography Engineering, 2014.
Attacker strategy evolution (GANet)
Last update: 08.01.2016
Contact: Zdenek Říha zriha@fi.muni.cz
Project description: This project focuses on automated generation of attacker's strategies against real implementation of various network applications. Currently, we aim to optimize existing Denial of Service attacks (DoS attacks, Link) in order to achieve maximum impact on the victim webserver. GANet contains source codes we are using - for now, combination of OS apps (Perfmon,…) and Python scripts.
- Research project internal wiki pages
- Project Github repository, wiki pages
- Zdenek Říha 2016-now (?) zriha@fi.muni.cz;
- Víťa Bukač 2014-now (preparation of HTTP DOS experiments, VM preparation, initial Python implementation)
- Radim Ošťádal 2014-now (preparation of HTTP DOS experiments)
- Petr Švenda 2014-now (gibbering)
Former participants: Tatevik Baghdasaryan 2014-2015 (testing simple web server);
Selected publications
- [2015] Bukač, V.; Ošťádal, R.; Švenda, P.; Baghdasaryan, T. and Matyáš, V.: Challenges of fiction in network security - perspective of virtualized environments, LNCS 9379, pp. 145-151, Springer, 2015.
- [2014] Bukač, V.; Lorenc, V. and Matyáš, V.: Red Queen's Race: APT win-win game. In Security Protocols XXII - 22nd International Workshop, Revised Selected Papers, LNCS 8809, pp. 55-61, Springer, 2014.
Whitebox cryptography
Last update: 14.9.2015
Status: Completed/On hold
Contact: Petr Švenda svenda@fi.muni.cz
Project description: This project is focused on design and development of the special implementations of cryptographic functions able to operate in an environment under full control of an attacker and still able to protect used secrets (e.g., encryption keys).
- Research project internal wiki pages
- SecureFW framework for source codes and binaries - earlier version of whitebox AES implementation in Cpp, secure channel with JavaCard smart card
- Explanation of whitebox cryptography, homomorphic encryption and computation with encrypted function/data: slides
- List of resources related to whitebox cryptography
- Lenka Bačinská 2012-now (Whitebox AES)
- Petr Švenda 2008-now (project lead, whitebox AES with smartcards)
Former participants: Marián Čečunda 2013-2015 (Whitebox RSA, HMAC, Keccak); Dušan Klinec 2012-2014 (whitebox AES implementation, attacks);
Selected publications
- [2015] Bačinská, L.: White-box attack resistant cipher based on WBAES, Master thesis, Masaryk university, 2015.
- [2015] Čečunda, M.: Návrh implementace algoritmů RSA a HMAC pomocí whitebox kryptografie, Master thesis, Masaryk university, 2015.
- [2013] Klinec, D.: White-box attack resistant cryptography, Master thesis, Masaryk university, 2013.
DDoS-as-a-Service landscape
Last update: 14.1.2016
Status: Completed/On hold
Contact: Vít Bukač xbukac@fi.muni.cz
Project description: We want to map the dark economy behind Denial-Of-Service attack services (DDoSaaS) for hire, the communication between DDoSaaS providers and customers and collect samples of attack traffic from real existing DDoS services. This project is about getting hands-on experience with network attacks in real environment instead of in closed labs, analyzing often neglected economy aspect of network attacks and dipping into the mindset of a cyber-criminal.
- Research project internal wiki pages
- Vít Bukač 2014-2015 (Coordinator)
- Vlasta Šťavová 2014-2015 (Social aspects)
- Lukáš Němec 2014-2015 (Technical aspects)
- Zdeněk Říha 2015 (Technical aspects)
- Lukáš Šrom 2014 (Technical aspects)
Publications
- [2015] Bukač, V.; Šťavová, V.; Němec, L.; Říha, Z. and Matyáš, V.: Service in denial – clouds going with the winds, In Proceedings of NSS 2015, 9th International Conference on Network and System Security, LNCS 9408, pp. 130-147, Springer, 2015.
- [2015] Bukač, V. and Matyáš, V.: Analyzing traffic features of common standalone DoS attack tools, In Proceedings of SPACE 2015, 5th International Conference on Security, Privacy, and Applied Cryptography Engineering, LNCS 9354, pp. 21-40, Springer, 2015.
- [2015] Bukač, V.; Říha, Z.; Šťavová, V. and Matyáš, V.: DDoSaaS: DDoS jako služba, In IS2: From trends to solutions, pp. 35-39, Tate International, 2015.
Android Security
Last update: 14.10.2014
Status: Completed/On hold
Contact: Zdeněk Říha zriha@fi.muni.cz ; Dušan Klinec ph4r05@mail.muni.cz
Project description: These activities look at the security issues of the Android installation files (APK). The Android APK files are digitally signed, but the signer can be anybody. Therefore it is possible to to modify the APK files (to include malware, for example) and resign it. This can be done in an automated way. Such a modification/infection can also be done online in the form of the man-in-the-middle attack where the APK package is transparently modified on its way from the server towards the mobile device if no encryption of the communication is done.
- Zdenek Říha 2012-now
- Dušan Klinec 2014-now
Former participants: Jan Svoboda (2013-2014), Eduard Cihuňka (2013-2014)
Selected publications