Architecture Considerations for Massively Parallel Hardware Security Platform - SPACE 2015
Authors: Dan Cvrcek, Petr Svenda
Abstract: Cryptography as a service (CaaS) provides means for executing sensitive cryptographic operations when the primary computing platform does not offer the required level of trust and security. Instead of executing operations like document signing directly by an application running in untrusted environment, the operation keys are only present in trusted environment used by CaaS. Once the operation keys are put in place, the applications use a CaaS interface to obtain results of sensitive operations –- document signatures -– executed by CaaS. A typical scenario is the use of virtual computing platform in the cloud. Use of CaaS reduces impact of the potential compromise of this virtual platform and simplifies subsequent recovery. The attacker will not learn the value of sensitive keys (e.g., signing keys) and is only able to use the keys for a limited time. The CaaS is enabling technology for a large number of use cases where security is important. The concept of scalable and universally available CaaS has also far-reaching usability, security, legal, and economics consequences of cloud use. In this position paper, we focus on requirements for building a CaaS platform – what are the options and challenges to build hardware and software components for CaaS suitable for usage scenarios with different load patterns and user requirements. We propose a suitable architecture for CaaS that can be shared by a large number of concurrent users, i.e., providing access to a large number of cryptographic keys. We also provide practical results from our prototype implementation.
- Conference page: SPACE 2015
- Download author pre-print of the paper: pdf
- Download presentation: pdf
- Download used source codes: JCAlgTest on GitHub
- More info about supported algorithms on smart cards: JavaCard algorithm support list (40+ cards)
Bibtex:
@inproceedings{cryptohive_caas_space2015,
author = {Dan Cvr\v{c}ek \and Petr \v{S}venda},
title = {Architecture Considerations for Massively Parallel Hardware Security Platform},
booktitle = {The 5th International Conference on Security, Privacy, and Applied Cryptography Engineering
(SPACE’2015), LNCS 9354},
year = {2015},
pages = {269--288},
doi = {10.1007/978-3-319-24126-5_16},
publisher = {Springer}
}
What is this paper about?
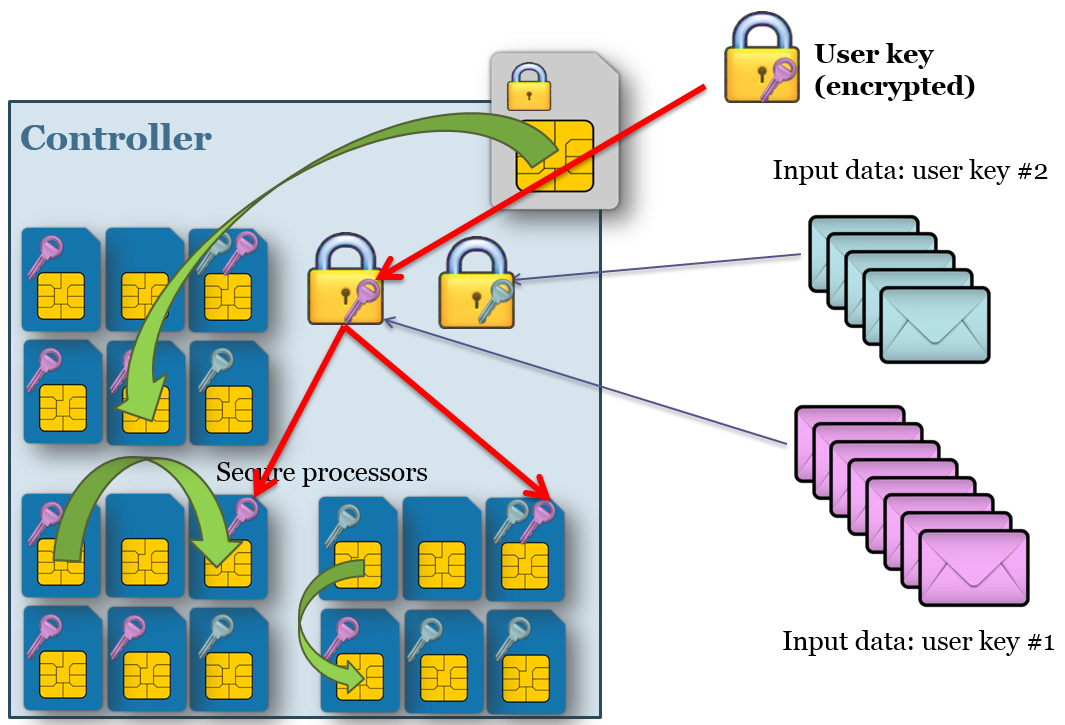
The focus of this work is description, analysis and prototype implementation of hardware security architecture, which can:
- support high number of parallel users with many different cryptographic keys,
- provide high performance for a cryptography as a service,
- yet withstand a skilled attacker with direct physical access to target device.
The typical usage scenario is high speed security box in datacenter shared by many users without need for trust put in security box operator. The architecture utilizes grid of cryptographic smart cards interconnected by secure channels.