Research: Analysis of Trusted Platform Module chips
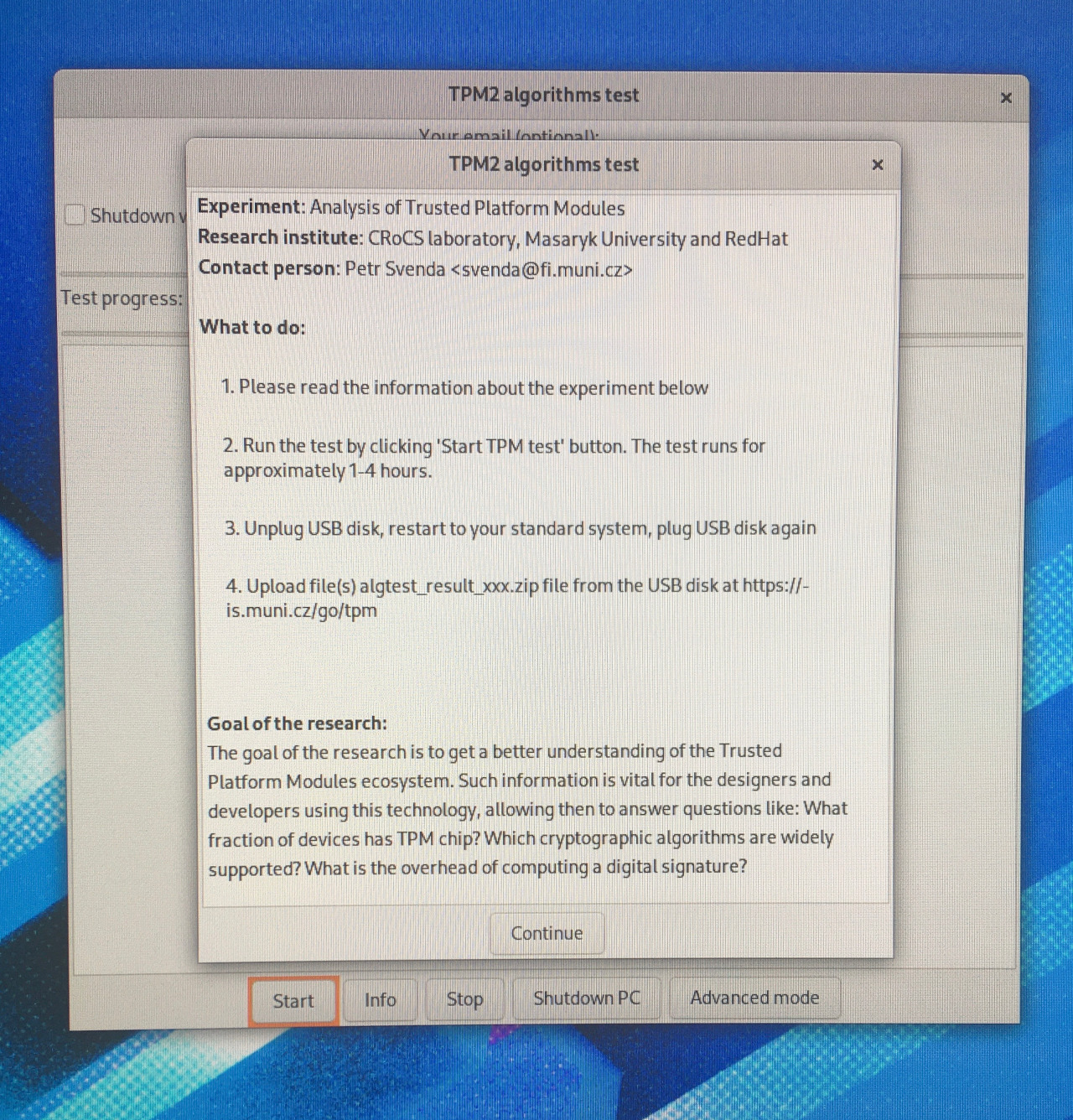
The goal of the research is to get a better understanding of the Trusted Platform Modules ecosystem. Such information is vital for the designers and developers using this technology, allowing then to answer questions like: What fraction of devices has TPM chip? Which cryptographic algorithms are widely supported? What is the overhead of computing a digital signature?
The research consist of two primary steps:
- Collection of raw data about TPM chips deployed in real-world devices like notebooks, desktops, and servers (the part we are asking you for kind help).
- Analysis of the data collected to provide insight into the TPM ecosystem (done by us, resulting in a summary of the most important findings, scientific paper, and research dataset available for replicability and further research).
How to collect data via Live Bootable Image
The data collection consists of 3 principal steps:
- Preparation of bootable USB drive (20 minutes to download image and 10 minutes to setup)
- TPM data collection (1-3 hours) using live image
- Send collected data (anonymous upload, email)
- (step 2., and 3., can be repeated for multiple computers, no need to create USB drive again)
1. Preparation of bootable USB drive
Duration: Preparation of bootable device will take approximately 20 minutes to download image and 10 minutes to setup.
- Prepare an empty USB drive with at least 4GB size (IMPORTANT: all content will be erased)
- Download live USB image: algtest-usb-disk.img and save to disk (e.g., folder C:\TPM\)
- Download and install Balena Etcher (Windows, Linux, Mac) to create bootable USB drive. (Alternatively, you may use Rufus instead (Windows only)).
- Run Balena Etcher, click Select image and browse for previously downloaded algtest-usb-disk.img on your disk
- Insert empty USB drive, click Select target and pick the USB disk
- (double-check that displayed drive is your intended USB drive – check the label, check size)
- Click Flash! and wait approximately 5 minutes until flashing is completed.
2. Data collection
Duration: Running Fedora-based system from the bootable device and data collection will take approximately 2-3 hours.
- Place your computer to steady location (on the desk) and plug in power cable.
- Insert installed USB drive from step 1 into the computer and restart your machine.
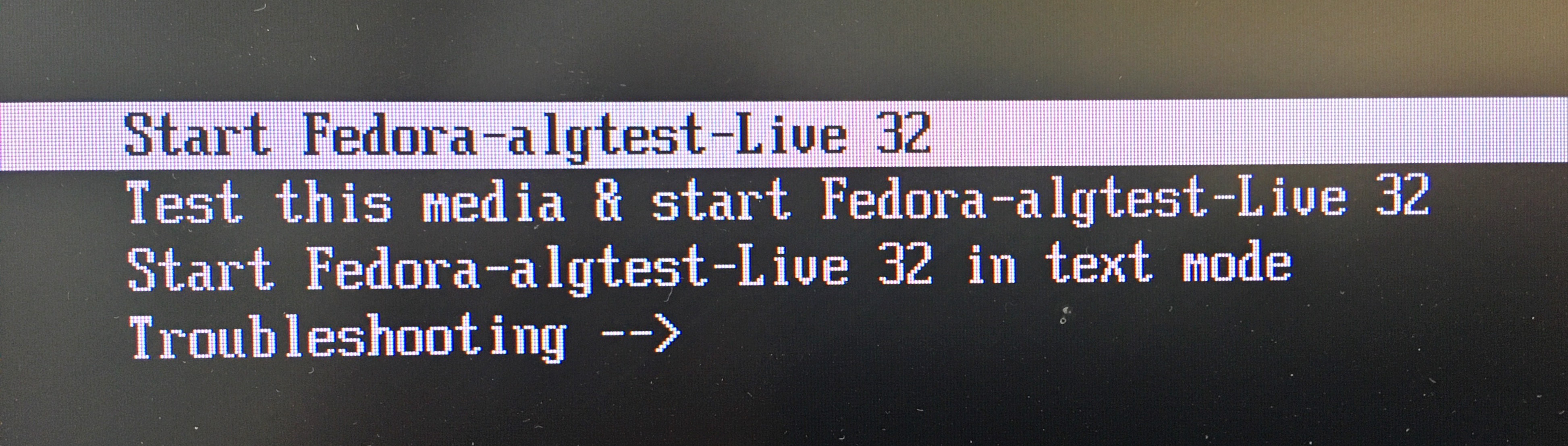
- If prompted, select boot from USB device instead of standard disk. Select Start Fedora-algtest-Live 32 boot option.
- Wait until Fedora-based TPM testing system is booted. Read the summary of the data we are collecting.
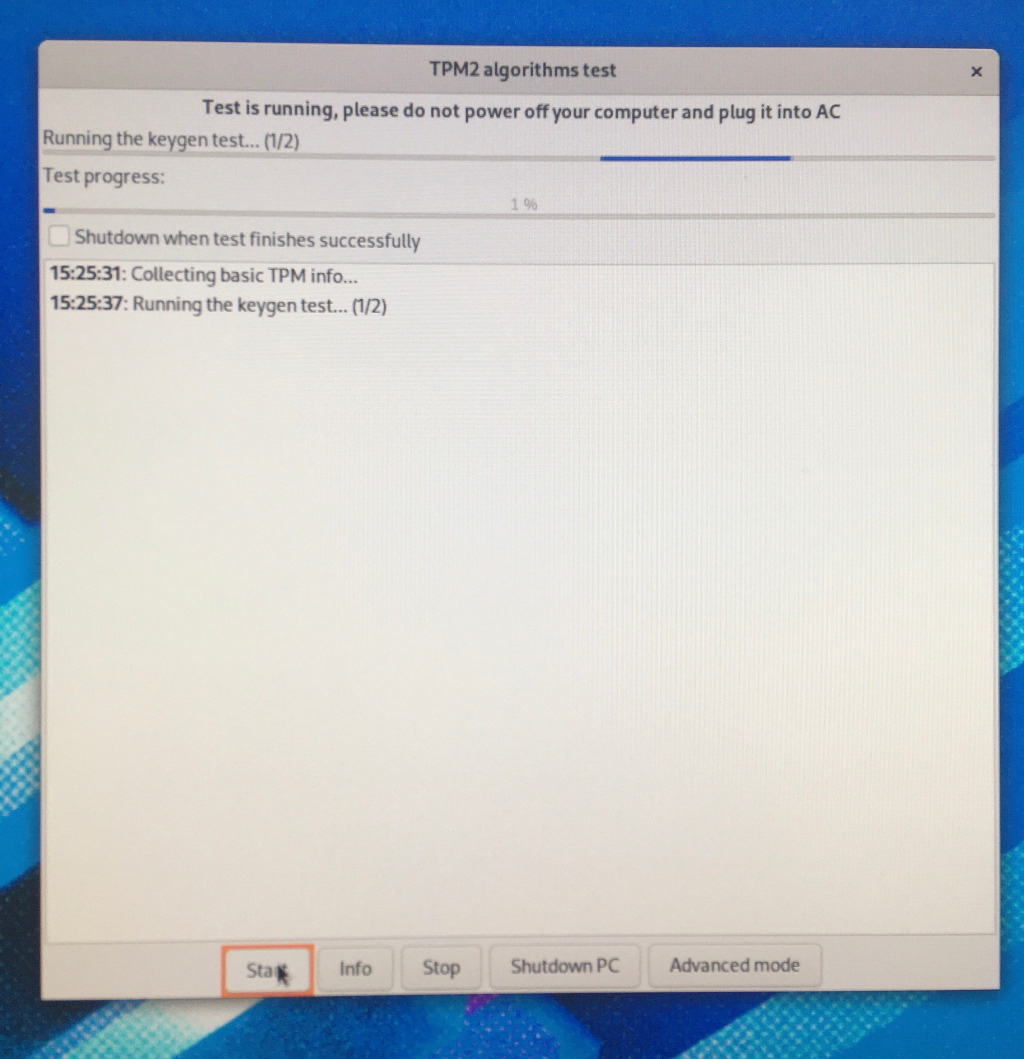
- Press the Start button
- Check that test started and is running (Log window contains 'XX:YY:ZZ Collecting basic TPM info…').
- Wait for 2–3 hours until the test is finished (100% Test progess).
- IMPORTANT: If test will not finish even after 5 hours and no visible progress is seen, please press the Stop button and continue to upload the partial results.
- Press the Shutdown PC button; wait until your machine is stopped. Unplug the USB drive.
- Restart your computer to your standard environment
3. Submit collected data
- Make sure the USB drive is unplugged.
- Start into your standard environment (e.g., Windows, Linux).
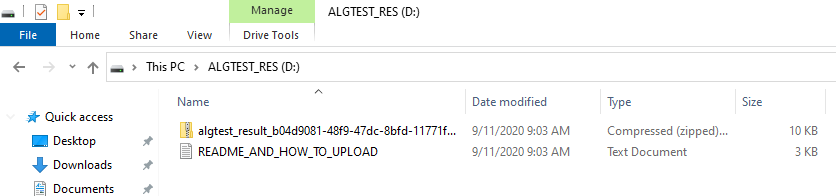
- Plug the USB drive, new drive with label
algtest_resis mounted (e.g., 'E:\'). - Locate file(s) with a file name in the form of
algtest_result_xxxxxx-xxxx-xxxx-xxxx-xxxxxxxx.zip. - Visit page
https://is.muni.cz/dok/depository_in?lang=en;vybos_vzorek=4085and follow instructions how to upload the file (no authentication required, just drop the files). Alternatively, send email to Petr Svenda tpm.crocs@gmail.com with filealgtest_result_xxx.zipattached.
Troubleshooting
Issue: Solutions below does not solve the problem
Solution: If you have any issue which solutions below will not help with, please notify us at tpm.crocs@gmail.com.
Issue: The bootable image cannot be downloaded
Solution: Download from the secondary backup location. Please notify us at tpm.crocs@gmail.com.
Issue: The live Fedora system will not start to boot
Solution: Go to BIOS (press F1, F8, F12, Enter or special button depending on your computer), select alternative boot device (USB you flashed) and continue
Issue: The live Fedora system will stop with error during boot
Solution: Try to change USB slot used to insert bootable USB disk, try to put device into stable position to prevent interruption of communication to USB disk
Issue: The TPM data collection will start, but finish very quickly (less than 10 seconds) with error 'Cannot collect TPM 2.0 info. Your TPM may probably be disabled in BIOS or you do not have a TPM 2.0.'
Solution 1: Restart your computer, enter BIOS (press F1, F8, F12, Enter or special button right), enable option named as 'TPM chip', 'Security chip' or similar. Then try to boot from USB again.
Solution 2: Try to update your BIOS if possible (older BIOSes are known to have incompatibility with some TPM chips under Linux). Then restart and boot from USB again.
Please submit the results even if the error persists.
Issue: I want to see the source code and build live image myself
Solution: You are more than welcome, please visit https://github.com/danzatt/tpm2_algtest_live for live image builder repository and https://github.com/danzatt/tpm2-algtest (collection tool itself).
Research details
Primary contact: doc. Petr Svenda <svenda@fi.muni.cz>
Research institute: CRoCS laboratory, Masaryk University and Red Hat Czech
Collected data:
Data we collect:
- Device vendor, type (e.g.,
Lenovo ThinkBook 15) and BIOS version. - TPM vendor, firmware version (e.g.,
Intel 401.1.0.0) and TPM version-related information. - TPM metadata (
TPM_PT_xxxproperties likeTPM_PT_REVISION,TPM_PT_MANUFACTURERorTPM_PT_PCR_COUNT– see fileQuicktest_properties-fixed.txtandQuicktest_properties-variable.txtfor full list). - Algorithms and commands supported by TPM (
TPMA_ALGORITHMandTPMA_CC properties, seeQuicktest_algorithms.txtandQuicktest_commands.txtfor full list). - Performance measurements for various cryptographic algorithms (see
Perf_xxx.csvfiles). - Freshly generated, transient keys for ECC and RSA (see
Keygen_ECC_xxx.csvandKeygen_RSA_xxx.csv). - Note: All mentioned files are stored inside the
algtest_result_xxx.zipfile.
Data we do NOT collect:
- Personal information about the user of the computer analyzed.
- Endorsement key.
- Attestation key(s).
- User-specific content of the non-volatile TPM memory (NVRAM).
Data retention:
- We plan to release the data collected as open research dataset to enable wider research cooperation.
- The data collected will be first analyzed by CRoCS research team for the purpose of analysis current TPM chip ecosystem. We plan to release the data collected together with the research findings.