This is an old revision of the document!
On Secrecy Amplification Protocols - WISTP2015
Authors: Radim Ostadal, Petr Svenda, Vaclav Matyas
Abstract: We review the most important secrecy amplification protocols, which are especially suitable for ad-hoc networks of devices with limited resources, providing additional resistance against various attacks on used cryptographic keys without necessity for asymmetric cryptography. We discuss and evaluate different designs as well as approaches to create new protocols. A special focus is given to suitability of these protocols with respect to different underlying key distribution schemes and also to open research questions.
- Conference page: WISTP 2015
- Download paper: pdf
- Download extended version of paper: FIMU-RS-2015-01 (technical report, FI MUNI)
- Download presentation: pdf
- Download used simulator and configuration files: zip source code, executable file
Bibtex:
@inproceedings{secrecyamplif_wistp2015,
author = {Radim O\v{s}\v{t}\'{a}dal and Petr \v{S}venda and V{\'a}clav Maty{\'a}\v{s}},
title = {On Secrecy Amplification Protocols},
booktitle = {The 9th WISTP International Conference on Information Security Theory and Practice (WISTP’2015),
LNCS 9311},
year = {2015},
pages = {3--19},
doi = {10.1007/978-3-319-24018-3 1},
publisher = {Springer}
}
What is this paper about?
The secrecy amplification protocol provides description how messages with a fresh key material should be propagated inside a target network to turn provide secure link key to nodes with key compromised by an attacker. As wireless networks running on batteries are targeted, not only protocol's success rate (number of newly secured links), but also message overhead (significantly impacting energy consumption) must be considered.
In this we paper, we:
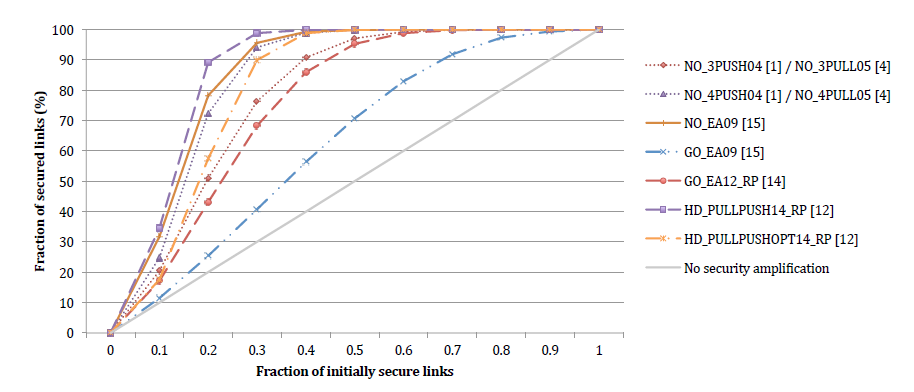
- Gave motivation, why secrecy amplification protocols should be used – if enough neighbours are available in network and random compromise pattern is assumed, network with only 30 % secure can be turned into network with more then 95 % secure links.
- Provided survey of all published secrecy amplification protocols (13 in total).
- Compared protocols wrt message efficiency, number of links they are able to secure and other characteristics.
- Discussed how hard is to execute secrecy amplification protocol in practice on real node (TelosB, TinyOS).
- Introduced new class of hybrid secrecy amplification protocols, which are easier to synchronize and provide very good tradeoff between number of secure links (higher the better) and messages transmitted (lower the better).
Increase in the number of secured links after SA protocols in the random compromise pattern on network with 20.3 legal neighbours on average. With in- creasing number of neighbouring nodes the general effectiveness of protocol grows. As can be seen, a strong majority of secure links (> 90%) can be obtained even when the initial network had 70% of compromised links.
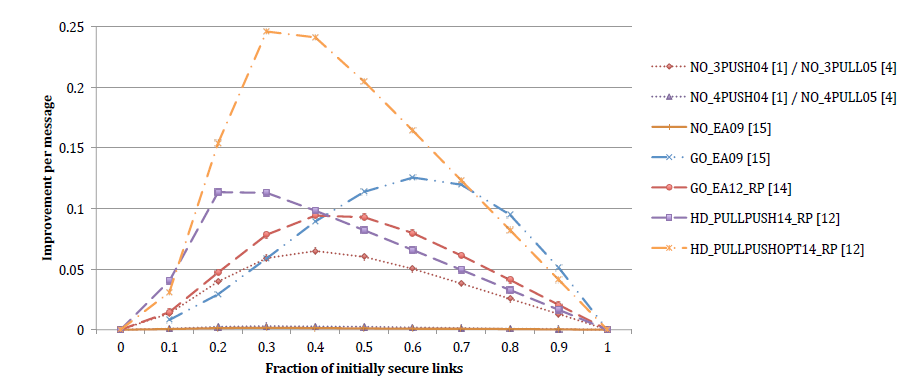
Increase in the number of secured links divided by the number of exchanged messages during the protocol execution (random compromise pattern, 20.3 legal neighbours on average). Node-oriented protocols send significantly more messages with rising network density. This stands especially for 4-party node-oriented protocols, which are the least effective. The best tradeoff shows group-oriented and hybrid protocols.