This is an old revision of the document!
New results on reduced-round Tiny Encryption Algorithm using genetic programming
Authors: Karel Kubicek, Jiri Novotny, Petr Svenda, Martin Ukrop
<note tip>This paper is not published yet, therefore page is not yet finalzed</note> Abstract: Analysis of cryptoprimitives usually requires extensive work of a skilled cryptanalyst. Some automation is possible, e.g. by using randomness testing batteries such as Statistical Test Suite from NIST (NIST STS) or Dieharder. Such batteries compare the statistical properties of the function’s output stream to the theoretical values. A potential drawback is a limitation to predefined tested patterns. However, there is a new approach – EACirc is a genetically inspired randomness testing framework based on finding a dynamically constructed test. This test works as a probabilistic distinguisher separating cipher outputs from truly random data. In this work, we use EACirc to analyze the outputs of Tiny Encryption Algorithm (TEA). TEA was selected as a frequently used “benchmark” algorithm for cryptanalytic approaches based on genetic algorithms. In this paper, we provide results of EACirc applied to TEA ciphertext created from differently structured plaintext. We compare the methodology and results with previous approaches for limited-round TEA. A different construction of EACirc tests also allows us to determine which part of cipher’s output is relevant to the decision of a well-performing randomness distinguisher.
- Journal page: Infocommunication journal.
- Download used version of EACirc tool and configuration files: zip source code, executable file or current version from github.
Bibtex:

@inproceedings{secrecyamplif_wistp2015,
author = {Radim O\v{s}\v{t}\'{a}dal \Petr \v{S}venda \and V{\'a}clav Maty{\'a}\v{s}},
title = {On Secrecy Amplification Protocols},
booktitle = {The 9th WISTP International Conference on Information Security Theory and Practice (WISTP’2015),
LNCS 9311},
year = {2015},
pages = {3--19},
doi = {10.1007/978-3-319-24018-3 1},
publisher = {Springer}
}
What is this paper about?

Automatized randomness testing is useful for checking one of the expected cipher properties – output ciphertext should be indistinguishable from a stream of truly random data. The common way to automate testing of randomness is using statistical batteries. But the limitation of the standard batteries for randomness testing is the fact they implement a fixed set of tests and can detect only a limited set of patterns and statistical irregularities.
In this work we use EACirc as a framework for constructing empirical tests of randomness. Capabilities of EACirc are compared with previous results as well as conventional statistical batteries analysing Tiny Encryption Algorithm.
EACirc consistently performs better than NIST STS. Dieharder is able to detect small deviances in one additional round. But analysis of EACirc output can provide information valuable for the cipher’s designer. We analyzed successful randomness tests and found the weak byte of limited TEA output.
In this we paper, we:
- Gave motivation for randomness testing and provided comparison of available tools.
- Summarized approach of previous works based on evolution algorithms and extended it by our approach.
- Analyzed TEA limited to 1 to 5 rounds with different plaintext types using both statistical batteries and EACirc.
- Interpreted various results from statistical batteries and EACirc on different plaintext types.
- Compared performance and data usage for many experiments settings.
- Analyzed resulting randomness test created by EACirc.
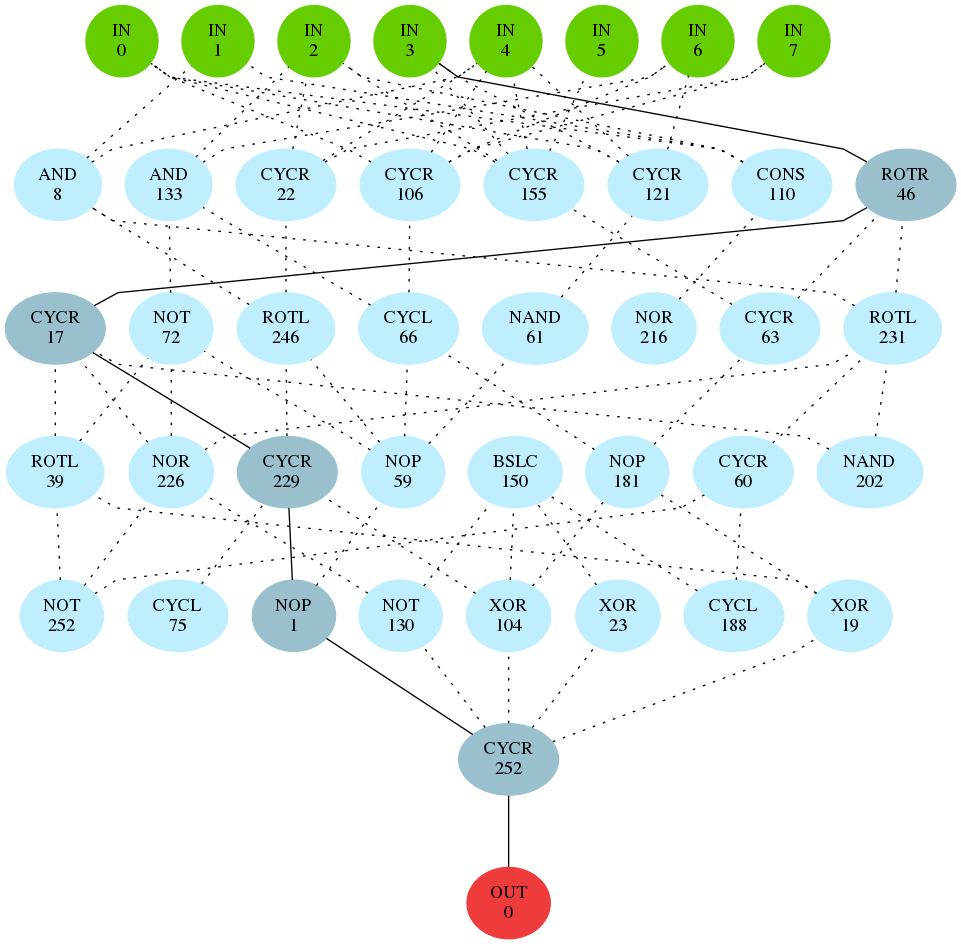
Figure showing increase in the number of secured links after secrecy amplification protocols in the random compromise pattern on network with 20.3 legal neighbours on average. With in- creasing number of neighbouring nodes the general effectiveness of protocol grows. As can be seen, a strong majority of secure links (> 90%) can be obtained even when the initial network had 70% of compromised links.

Figure showing increase in the number of secured links per message used during the protocol execution (random compromise pattern, 20.3 legal neighbours on average). The higher value is better - more links are secured per single message. Node-oriented protocols send significantly more messages with rising network density making them less effective per single message. This stands especially for 4-party node-oriented protocols, which are the least effective. The best tradeoff shows group-oriented and hybrid protocols.